PowerShell Module for Detecting Vulnerabilities to Speculative Execution
Microsoft today (Jan. 4th, 2018) provided a PowerShell module to detect vulnerabilities related to Speculative Execution side-channel attacks. This vulnerability affects Intel, AMD and ARM processors, along with operating systems. You can review the Microsoft security advisory ADV18002 here.
This will install the module to your local machine
Install-Module SpeculationControl
*if you are having issues with install the module via the command above you can find the module on my github here.
Get-SpeculationControlSettings
The above command will analyze your system and will show you the vulnerabilities that are present on your system as seen below in the image.
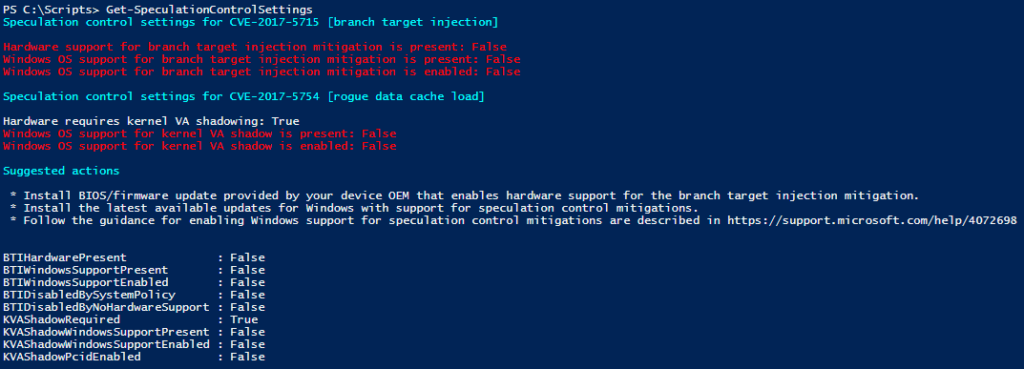
Currently this module works on Windows 10 (RTM, 1511, 1607, 1703, 1709), Windows 8.1, and Windows 7 SP1. The following link (here) will show all some additional information from Microsoft about the module and fixes.
-Stuart
*Update: From William Lam’s Twitter Account (Thanks Erik) – Link
- See https://kb.vmware.com/s/article/52264 for VMware Appliances
- ESXi 5.5 patches in works, no ETA
- VC patch in works to deliver Microcode update for EVC, no ETA
- More detailed FAQ will be published in coming week now that Embargo is lifted
*Update 2: From William Lam’s Twitter Account Link
https://kb.vmware.com/s/article/52245 – New top level VMware KB has just been published covering all things related to #Spectre & #Meltdown
Could you please share the script ?
Tina,
I have uploaded the module that was downloaded with the command to my Github. Look for the SpeculationControl.zip file, this includes all of the files needed to then import the module to run it.
-Stuart
Have you been successful in running this script on a Windows VM running on ESXi?
Even after the BIOS/ROM update it fails the hardware support check part of the script, but if I run it on Windows running bare metal it shows all green.
Erik,
I have ran the module on a VM, but it fails as well. My team and I have just started to plan for updating the ESXi hosts to the latest patch that is required to fix this issue.
From reading about this the correct order to patch for this is to start with the ESXi, then install the antivirus update, then finish with the OS level patches.
-Stuart
Thanks Stuart,
We decided to do it in parallel since more than one team is involved. Done with most of the antivirus and OS level patches, then about halfway done with ESXi and BIOS/ROM patching.
So getting eager for all green for my VMs. I will write here again if I discover how to achieve it.
Looks like an EVC update is needed, which is not out yet; https://twitter.com/lamw/status/949662333038559232
Finally got an all green, have to install the patches released yesterday, both VC and ESXi; https://www.vmware.com/security/advisories/VMSA-2018-0004.html
All host in the cluster must be upgraded, then it raises the EVC setting, and then the VMs need a cold start(to reload EVC mode for the VM)
Awesome news! Just a question for you since you are fully complaint with the patches, have you notices any performance issues as stated in many of the articles?
-Stuart
In our clusters containing CPUs from 2015+ and BIOS/ROM updates I don’t see much difference. Our load is not static and business has continued as normal so new VMs have been provisioned during this time.
We are still working on the clusters with older CPUs. Looks like the BIOS/ROM update for those systems is not expected until February, so I fear a nasty performance hit there.
We made a halt in upgrading HW version to 11 and cold starting the VMs since the BIOS/ROM was recalled. No VMs have crashed so far, but not taking the risk for all of them.